Schools: Pay Attention to the New Hacker & Cyberbullying Tool Firesheep
Firesheep has garnered much attention in tech circles. The developer, by releasing this Firefox extension, is nudging web service providers to fix a problem that has been known but ignored for years. Services like Facebook depend on cookies to maintain connections with users, and Firesheep easily intercepts these cookies to take over someone else’s session. There are several aspects about this tool that warrant schools’ attention.
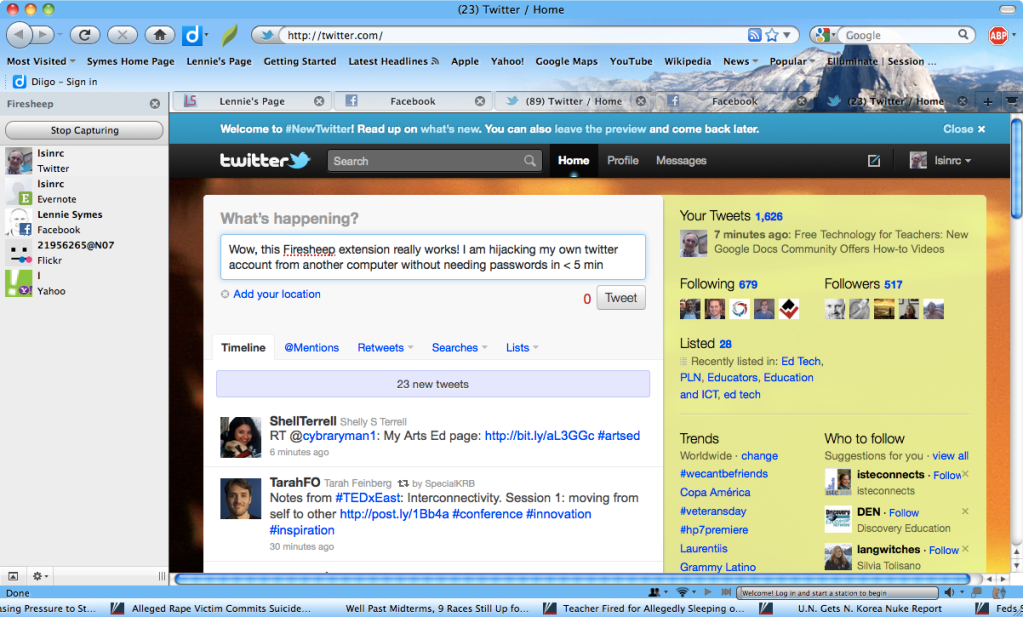
I tried Firesheep on an open wifi with a separate computer, and in less than five minutes I was able to hijack my own Twitter, Facebook, Flickr, Yahoo, and Evernote accounts with no passwords. I could take over the accounts and send messages or change settings, sometimes even passwords, just as if I were the person whose account I hijacked (okay, in this case I was)–this Twitter post for example:
Note on the left side Firesheep is showing all the sessions that are available for hijacking. It even provides account names and photos. I was the only one on the network, but if others were online I would be seeing their sessions as well.
The exploit is not new–for years we have had network sniffers to capture data on open networks–and web services have ignored this problem too long. The game changer here is how simple this new tool hijacks someone’s session.
The ease of this tool is amazing. On a Macintosh, this quick download had me scanning the network in seconds. On a Windows machine, there is an extra step of installing WinPCap first, but Youtube videos show the easy necessary steps to make it work.
This has ramifications for schools–not that students can do this on secure school networks, but most towns have businesses, or especially homes, with free/open wifi. A student sitting in any one of these open wifi businesses (or at the curb of a home with open wifi) can wreak havoc with another unsuspecting student or educator. A student with cyberbullying intentions can use this tool to send damaging messages impersonating the account owner or take over their account. Before this tool they had to weasel the password from the target student, now they just need to be in proximity.
Firesheep can be inhibited by using a WPA key, even a key everyone knows. According to Security Now, WPA utilizes inter-client isolation, so even posting the same WPA code for all to use will block this program from working. It might be in your school’s interest to approach businesses in town with open wifi to set up WPA codes and post them on the wall.
Some schools may think banning Firefox as their solution, but that is wrong thinking. All major browsers allow extensions, so this could have been made to work with any browser. I suspect more hacker tools like this will appear, at least until all web sites start using HTTPS/SSL kinds of connections.
So what should be the educator response? There are two main areas schools can be proactive. First, keep a closer ear on incidents of student accounts getting hijacked or cyberbullying. Even though most of these incidents will happen away from school, effective schools need to kill it quickly. Second, begin an education program for local businesses and homes to set up WPA on their wifi networks.
Some may think that spreading the word about this tool will plant the idea for students to use it, but that is also wrong thinking. You can never depend on student ignorance as your network security measure. While it is easy to think that shoring up security on non-school entities as “not our problem”, schools can get a lot of community good-will for a small amount of effort. Besides schools will have to deal with the problems generated from these unsecured networks, so make efforts to close down as many as possible.